
“Never trust, always verify.” This is the guiding principle of Zero Trust, one of the most reliable approaches to comprehensively protect your IT infrastructure.

Digital transformation presents companies with ever-evolving challenges – especially in cybersecurity. Traditional security approaches, which rely on strong perimeter protection, are no longer effective in a world where employees access cloud-based applications from anywhere. The traditional notion that everything within a corporate network is automatically secure is outdated.
This is where the Zero Trust principle comes into play: instead of blind trust, it relies on continuous verification of all access – regardless of whether users or devices are inside or outside the corporate network.
Ongoing digitalization brings unprecedented challenges for companies in the area of cybersecurity. Traditional security concepts, such as the castle-and-moat model – which focuses on strong perimeter protection – are outdated and create a false sense of security. In addition, modern ICT environments are characterized by a dynamic mix of local and cloud-based services. Employees increasingly work remotely, which leads to the classical network infrastructure being reduced more and more to pure connectivity functionality. These changes require new security strategies, as conventional perimeter protection mechanisms are no longer sufficient.
Zero Trust addresses these challenges by assuming that no user or device is inherently trustworthy – regardless of whether they are within or outside the corporate network.
The solutions available on the market make big promises, leading to the question: is Zero Trust just another marketing trick to sell products?
Quite the opposite! Zero Trust goes far beyond that and is not simply a buzzword used by vendors to promote their solutions. It is a comprehensive security concept that encompasses a wide range of measures – from technical implementations to organizational and cultural changes within a company.
Zero Trust requires a fundamental realignment of the security philosophy. Instead of relying on perimeter protection, this approach focuses on the continuous verification of all access. This means that trust is no longer assumed but must be constantly verified.
This shift affects not only technology but also processes and corporate culture. Although the core principles have now become established, Zero Trust remains a security concept that can be interpreted differently depending on perspective. Many product manufacturers continue to capitalize on the attention surrounding the topic and attempt to market their products under the Zero Trust label. This often leads to poor investments and a false sense of security.
A successful Zero Trust approach always requires a holistic view and integration of various security measures.
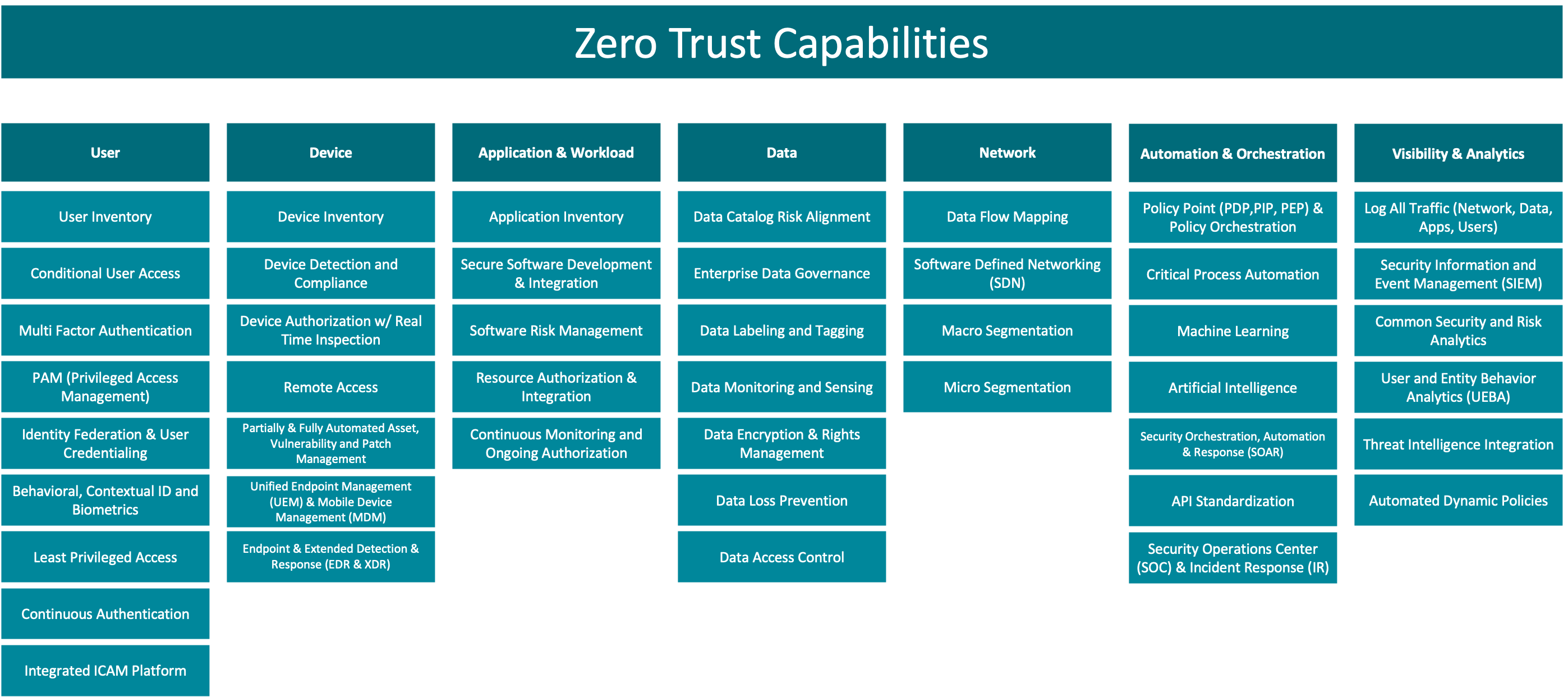
A structured yet iterative approach is crucial for the successful implementation of Zero Trust. The Zero Trust model of the Department of Defense (DoD) has proven itself in practice in various customer projects. It is based on seven different pillars, each of which includes specific capabilities. The goal is to continuously build these capabilities. However, the scope and prioritization of this development vary from company to company.
To implement Zero Trust effectively, companies should first conduct an assessment. This means evaluating the current status of the security architecture and understanding which capabilities are already in place and where there are gaps. Conduct your Zero Trust self-assessment here and compare your organization with others.
Next, a target state is defined that describes the desired security maturity and the required capabilities in each pillar. It is also important to recognize that different areas within a company have different requirements. For example, the security needs of customers and employees or of cloud and on-premises environments may vary. A tailored approach ensures that resources are used effectively and maximum security is achieved. With this foundation, a roadmap can be created that outlines in detail how the defined goals can be achieved. This plan should prioritize which capabilities should be developed first, based on the greatest benefit and highest risk.
This methodical approach ensures that the budget is used optimally and that Zero Trust is implemented where it provides the greatest value. The key question is not whether Zero Trust should be implemented, but how much of it is currently necessary. A gradual increase in maturity is sensible.
%20(4).png)
The individual pillars – users, devices, networks, and data – must not be viewed in isolation but as an interconnected whole. Complete and transparent capture of these elements is crucial. This includes continuous monitoring of current states, such as:
Visibility and analytics capabilities play a central role here. They allow real-time monitoring and assessment of all pillars. With this comprehensive visibility, companies can make informed decisions and identify potential risks early.
Based on these insights, adaptive and risk-based access decisions can be made. Policy enforcement is dynamic, based on current risk and defined security policies. For example, a device with outdated security status may be denied or restricted access.
To make this process efficient and scalable, automation and orchestration capabilities are used. They make it possible to seamlessly integrate the collected information into automated workflows. This allows access to be controlled in real-time and security measures to be implemented immediately, without manual intervention.
The cycle of visibility, analysis, policy enforcement, and automation creates a dynamic and adaptable security model. Through continuous monitoring and optimization of this cycle, companies can continually improve their security strategy and adapt to new threats.
The increasing complexity of modern IT environments and overarching digital business processes requires a rethink in security strategy. Zero Trust is by no means just a marketing gimmick; it offers a forward-looking approach that places identity and data at the center and leaves traditional security models behind.
It goes far beyond technical solutions and also includes organizational and cultural changes within the company. By strategically expanding their Zero Trust capabilities, companies can effectively address the growing challenges of digitalization.
Success lies in taking a holistic view and understanding that security is a dynamic process. Ultimately, it’s not a question of whether Zero Trust should be implemented, but to what extent and with what prioritization – always with the goal of ensuring security in a constantly changing world.
In additional blog posts, we will explore the individual phases of the FortIt Zero Trust Journey in more detail to help anchor Zero Trust sustainably in your organization.

